Pipelining in Computer Architecture Tutorial Study Notes with Examples
Pipelining
Pipeline processing is an implementation technique, where arithmetic sub-operations or the phases of a computer instruction cycle overlap in execution. A pipeline can be visualized as a collection of processing segments through which information flows.
The overlapping of computation is made possible by associating a register with each segment in the pipeline. The registers provide isolation between each segment.
General Structure of 3-Segment Pipeline

Each segment consists of a combinational circuit S, that performs a sub-operation over the data stream flowing through pipe. The segments are separated by register R, that hold the intermediate results between the stages.
- Information flows between adjacent stages under the control of a common clock applied to all the registers simultaneously.
- The behaviour of a pipeline can be illustrated with a space-time diagram. This is a diagram that shows the segment utilization as a function of time. The horizontal axis displays the time in clock cycles and the vertical axis gives the segment number.
- The space-time diagram shows the four segment pipeline with T1 through T6 six task executed

Technical Description
- Consider if K- segment pipeline with clock cycle time tp is used to execute n The first task T1 requires a time = Ktp.
- The remaining (n —1) tasks emerge from the pipe at the rate of one task per clock cycle and they will be completed after a time = (n —1)tp.
- Therefore, to complete n tasks using a K-segment pipeline requires K + (n —1) clock cycles.
- A non-pipeline unit perform the same operation and takes a time of to to complete each task. The total time required for n tasks in ntn.
- The speedup (S) is the ratio of a pipeline processing over an equivalent non-pipeline processing.
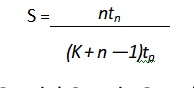
Special Case in Speedup
As number of tasks increases, n becomes larger than K-1, then K+ n-1 is approximately n. Then, speedup becomes
S= tn/tP„
If we assume tn= Ktp; S= ntP/tp =K
Instruction Pipeline
- Pipeline processing can occur not only in the data stream but in the instruction stream.
- An instruction pipeline reads consecutive instructions from memory while previous instructions are being executed in other segments.
- This causes the instruction fetch and execute phases to overlap and perform simultaneous operations and consider a computer with a instruction fetch unit and an instruction execution unit designed to provide two-segment pipeline.
- Computers with complex instructions requires other phases in addition to (etch and execute to process an instruction completely.
The instructions cycle is as follows.
- Fetch the instruction from memory
- Decode the instruction
- Calculate the effective address
- Fetch the operands from memory
- Execute the instruction
- Store the result in the proper place.
Difficulties in Instruction Pipeline
- Resource conflicts: It is caused by access to memory by two segments at the same time. Most of these conflicts can be solved by using separate instruction and data memories.
- Data dependency conflicts: It arises when an instruction depends on the result of a previous instruction but this result is not yet available.
- Branch difficulties arise: It arises from branch and other instructions that change the value of PC.
Key Points –
- The memory unit that communicates directly with the CPU is called the Main memory.
- Devices that provide backup storage are called auxiliary memory. e., magnetic tapes or magnetic disks.
Sorting in Design and Analysis of Algorithm Study Notes with Example
Follow Us On Cyber Point Solution Youtube Channel : Click Here
Follow Us on Social Platforms to get Updated : twiter, facebook, Google Plus
Learn More Ethical Hacking and Cyber Security click on this link. cyber security
