A Guide to Implement CIS Controls with PowerShell
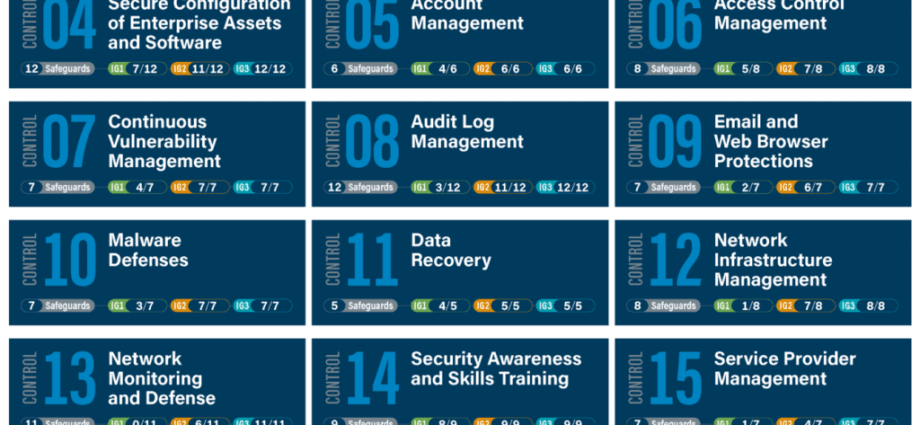
What is CIS? A Guide to Implement CIS Controls with PowerShell –Riya Jain In today’s interconnected world, cyber threats have become increasingly sophisticated, making it vital for organizations to adopt effective cybersecurity frameworks. The Center for Internet Security (CIS) provides a set of best practices known as the CIS Controls,Continue Reading
Step-by-Step Guide to Auditing Compliance via ManageEngine Endpoint Central
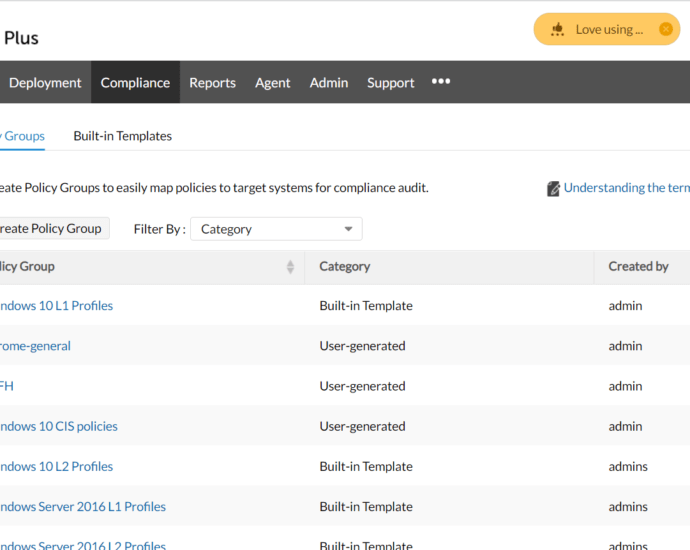
Step-by-Step Guide to Auditing Compliance via ManageEngine Endpoint Central –Riya Jain Maintaining security and compliance is essential for any organization, and ManageEngine Endpoint Central provides a powerful solution for automating and streamlining this process. Here’s a detailed guide on how to audit your environment using Endpoint Central. Step 1:Continue Reading
Understanding Fog Computing, Grid Computing, and Cloud Computing: A Comprehensive Guide
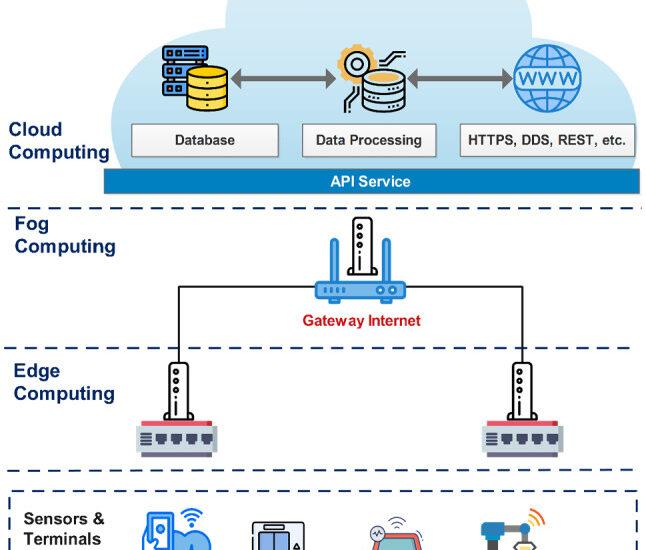
Understanding Fog Computing, Grid Computing, and Cloud Computing: A Comprehensive Guide –Riya Jain In today’s tech-driven world, various computing models are transforming the way businesses handle data and processes. Among the most significant are fog computing, grid computing, and cloud computing. Each of these models has distinct advantages, architectures, andContinue Reading
LLMNR poisoning – Active Directory security
LLMNR Poisoning: A Hidden Vulnerability in Windows Networks – Riya Jain In today’s enterprise environments, Windows-based networks rely heavily on Active Directory (AD) for managing resources and administrative tasks. However, with this convenience comes inherent risks, including one that is often overlooked—Link-Local Multicast Name Resolution (LLMNR) poisoning. This vulnerability canContinue Reading
Achieving ISO 27001 Compliance for Companies in Qatar: A Comprehensive Guide
Implementing ISO 27001 compliance in Qatar’s tech industry requires a detailed, tailored approach that addresses both global standards and local regulatory frameworks. Qatar’s booming technology sector, with its focus on digital transformation and cloud infrastructure, necessitates strict cybersecurity measures to protect sensitive data, ensure business continuity, and foster trust inContinue Reading
CSA STAR Program – 3 Levels
What is the CSA STAR Program? A Comprehensive Guide -Riya Jain The CSA STAR (Security, Trust, Assurance, and Risk) program is an essential certification framework for cloud service providers (CSPs) seeking to demonstrate their cloud security practices. As the adoption of cloud services grows, so does the need for robustContinue Reading
20 Must-Follow WordPress Security Steps for 2024
WordPress Security Steps WordPress is a widely used platform that powers over 43% of the web. However, its popularity makes it a prime target for cyberattacks. Following the right steps can significantly improve your website’s security and protect it from threats like brute-force attacks, malware, and phishing. –Riya Jain InContinue Reading
The Complete Guide to ISO 27001:2022 – Key Changes and How to Stay Compliant
ISO 27001:2022 – Key Changes -Riya Jain The latest iteration of ISO 27001, released in 2022, brings subtle but important changes to better align with other ISO management standards. While the number of clauses remains the same as in the ISO 27001:2013 version, several updates have been made to improveContinue Reading
How to implement STRIDE threat model – STRIDE GPT4
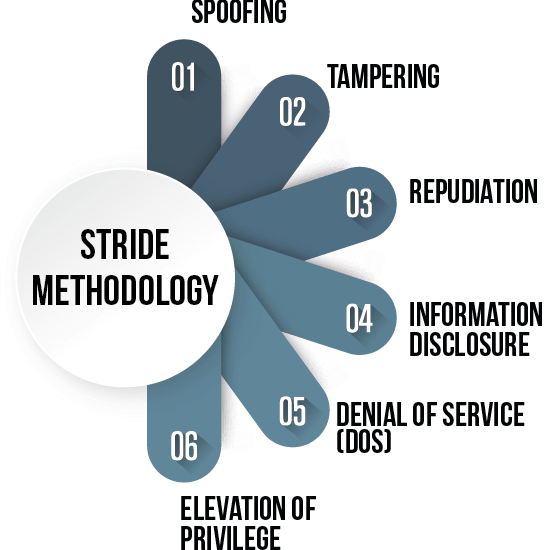
STRIDE: Understanding and Mitigating the Threat – Riya Jain STRIDE is frequently suited for use in object-oriented threat modeling, it was introduced by Microsoft and includes six classes of threats: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. It assists you in taking any component ofContinue Reading
Threat modelling : 4 Frameworks
What is Threat Modelling? Threat modelling is a crucial cybersecurity process used to identify, analyze, and mitigate potential security threats to an application, system, or organization. This practice helps individuals and security teams understand how potential attackers might operate, allowing them to develop effective countermeasures to prevent these threats fromContinue Reading