Computer Network Tutorial Study Notes for Beginners with Examples
Computer Network
A collection of computers (or computer like devices) that are able to communicate with each other through some medium, using hardware and software. Two computers (or computer like devices) are said to be connected, if they are able to exchange information or able to communicate.
Every network includes elements to enable data transfer or sharing are given below.
- At least two computers (or computer like devices)
- Network interfaces
- A connection medium
- Operating system, strategies, algorithms and protocols
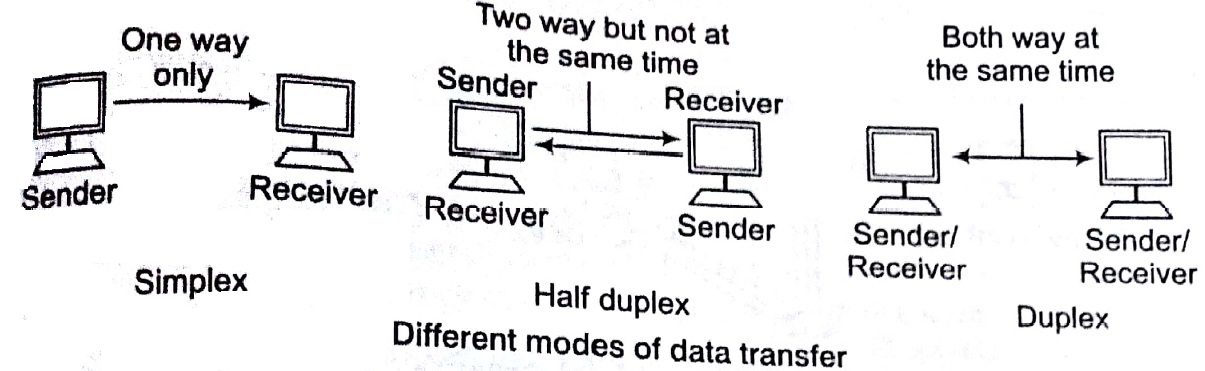
Data Transfer Modes
There are mainly three modes of data transfer
Simplex: Data transfer only in one direction e.g., radio broadcasting.
Half Duplex: Data transfer in both direction, but not simultaneously i.e., in one direction at a time e.g., talk back radio, CB radio (citizen band).
Full Duplex or Duplex Data transfer in both directions, simultaneously e.g., telephone.
Elements used in Computer Networks for Communication
Some basic elements which are using in communication systems of a computer network are given below
- Data Source: Provides the data to transmit.
- Sender: (Transmitter) Converts data to signals for transmission.
- Data Transmission System: Transmits the data e. , converted in signals.
- Receiver: Converts received signals to data.
- Destination: Receives and uses incoming data.
- Node: A device with independent communication ability and unique network address.
- Protocol: A formal description, comprising rules and conventions defines the method of communication between networking devices.
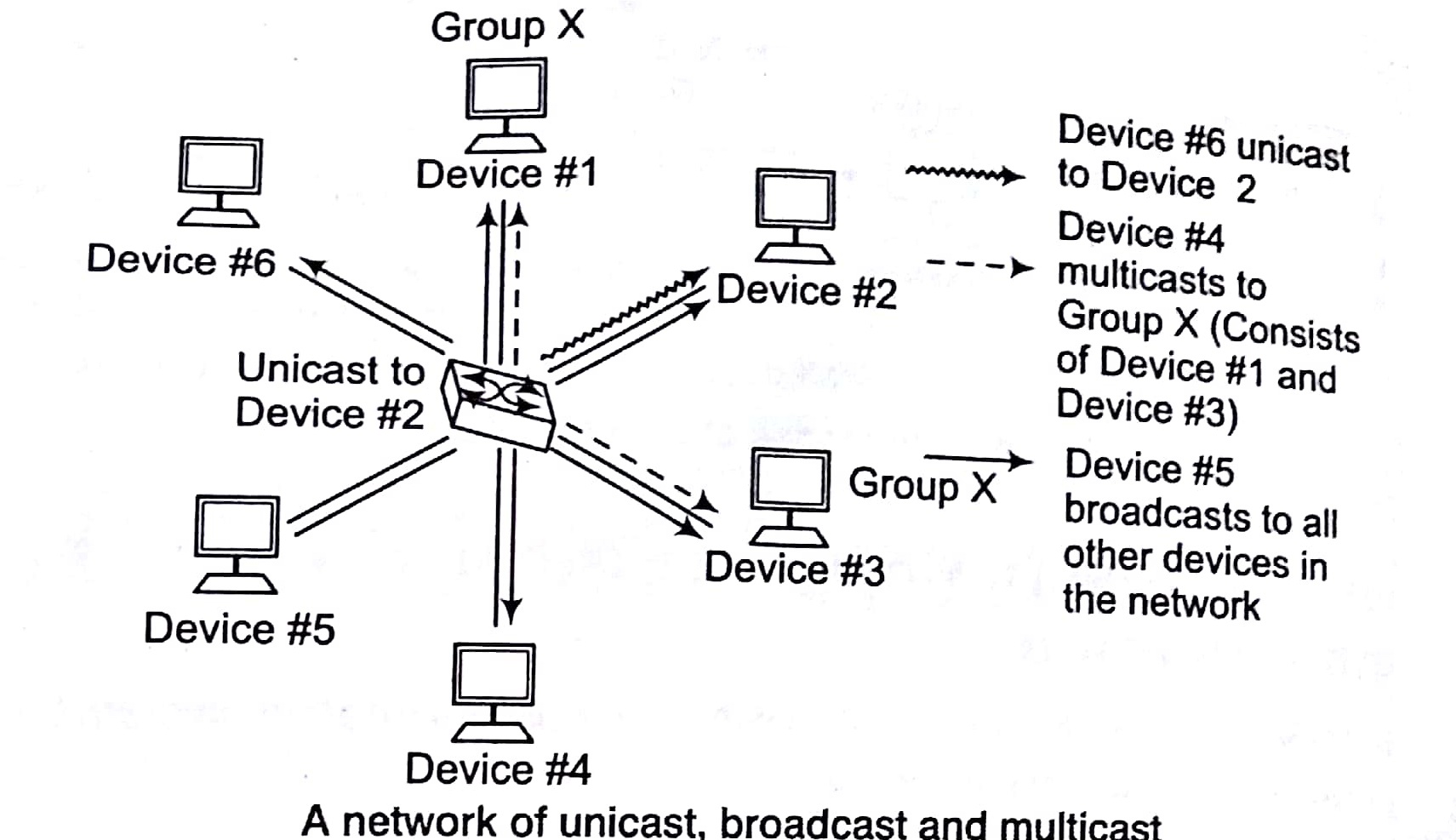
Methods of Message Delivery (i.e., Casting)
A message can be delivered in the following ways
Unicast: One device sends message to the other to its address.
Broadcast: One device sends message to all other devices on the network. The message is sent to an address reserved for this goal.
Multicast: One device sends message to a certain group of devices on the network.
Types of Networks
The types of network based ,on their coverage areas are as given below
LAN (Local Area Network )
LAN is privately owned network within a single building or campus. LANs can small, linking as few as three computers, but often link hundreds of computers used by thousands of people (like in some IT office, etc.)
An arbitration mechanism is installed in LAN to decide, which machine will use the access, when more than one machines are requesting for communication. LAN are used for connecting personal computers, workstations, routers and other devices.
Their main characteristics are given below
- Topology: The geometrical arrangement of the computers or nodes.
- Protocols: How they communicate.
- Medium: Through which medium.
MAN (Metropolitan Area Network)
A MAN covers a city. An example of MAN is cable television network in city
WAN (Wide Area Network)
A wide area network or WAN spans a large geographical area often a country.
Internet
It is also known as network of networks. The Internet is a system of linked networks that are world wide in scope and facilitate data communication services such as remote login, file transfer, electronic mail, world wide web and newsgroups etc.
Network Topology
Network topology is the arrangement of the various elements of a computer or biological network. Essentially it is the topological structure of a network, and may be depicted physically or logically. Physical topology refers to the placement of the network’s various components, inducing device location and cable installation, while logical topology shows how data flows within a network, regardless of its physical design.
The common network topologies include the following sections.
Bus Topology
In bus topology, each node (computer server, other computer like devices) is directly connected to a common cable.
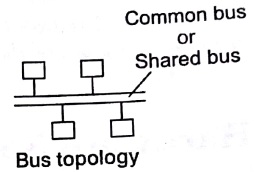
Note The drawback of this topology is that if the network cable breaks, the entire network will be down.
Star Topology

In this topology, each node has a dedicated set of wires connecting it to a central network hub. Since, all traffic passes through– the hub, it becomes a central point for isolating network problems and gathering network statistics.
Ring Topology
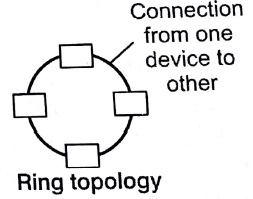
A ring topology features a logically closed loop. Data packets travel in a single direction around the ring from one network device to the next. Each network device acts as a repeater to keep the signal strong enough as it travels.
Mesh Topology
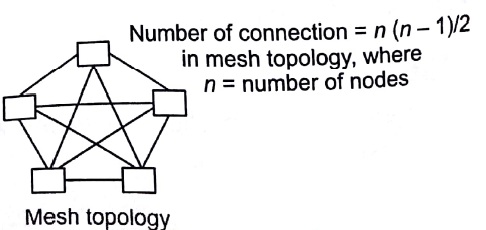
In mesh topology, each system is connected to all other systems in the network
Key Points
- In bus topology at the first, the message will go through the bus then one user can communicate with other.
- In star topology, first the message will go to the huh then that message will go to other user.
- In ring topology, user can communicate as randomly.
- In mesh topology, any user can directly communicate with other users.
Tree Topology
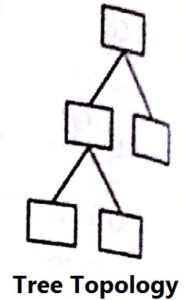
In this type of network topology, in which a central root is connected to two or more nodes that are one level lower in hierarchy.
Hardware/Networking Devices
Networking hardware may also be known as network equipment. computer networking devices. Some important networking devices used in the medium of communication are given below
Network Interface Card (NIC)
NIC provides a physical connection between the networking cable and the computer’s internal bus.
NICs comes in three basic varieties 8 bit, 16 bit and 32 bit. The larger number of bits that can be transferred to NIC, the faster the NIC can transfer data to network cable.
Repeater
Repeaters are used to connect together two Ethernet segments of any media type. In larger designs, signal quality begins to deteriorate as segments exceed their maximum length. We also know that signal transmission is always attached with energy loss. So, a periodic refreshing of the signals is required.
Hubs
Hubs are actually a multi port repeaters. A hub takes any incoming signal and repeats it out all ports. .
Key Points
- Repeaters provide the signal amplification required to allow a segment (cable) to be extended a greater distance.
- A typical repeater has just 2 ports, a hub generally has from 4 to 24 ports.
Different Types of Ethernet Network Table
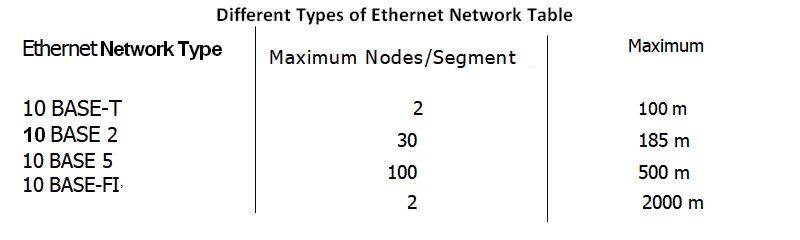
Bridges
when the size of the LAN is difficult to manage, it is necessary to breakup the network. The function of the bridge is to connect separate networks together Bridges do not forward bad or misaligned packets.
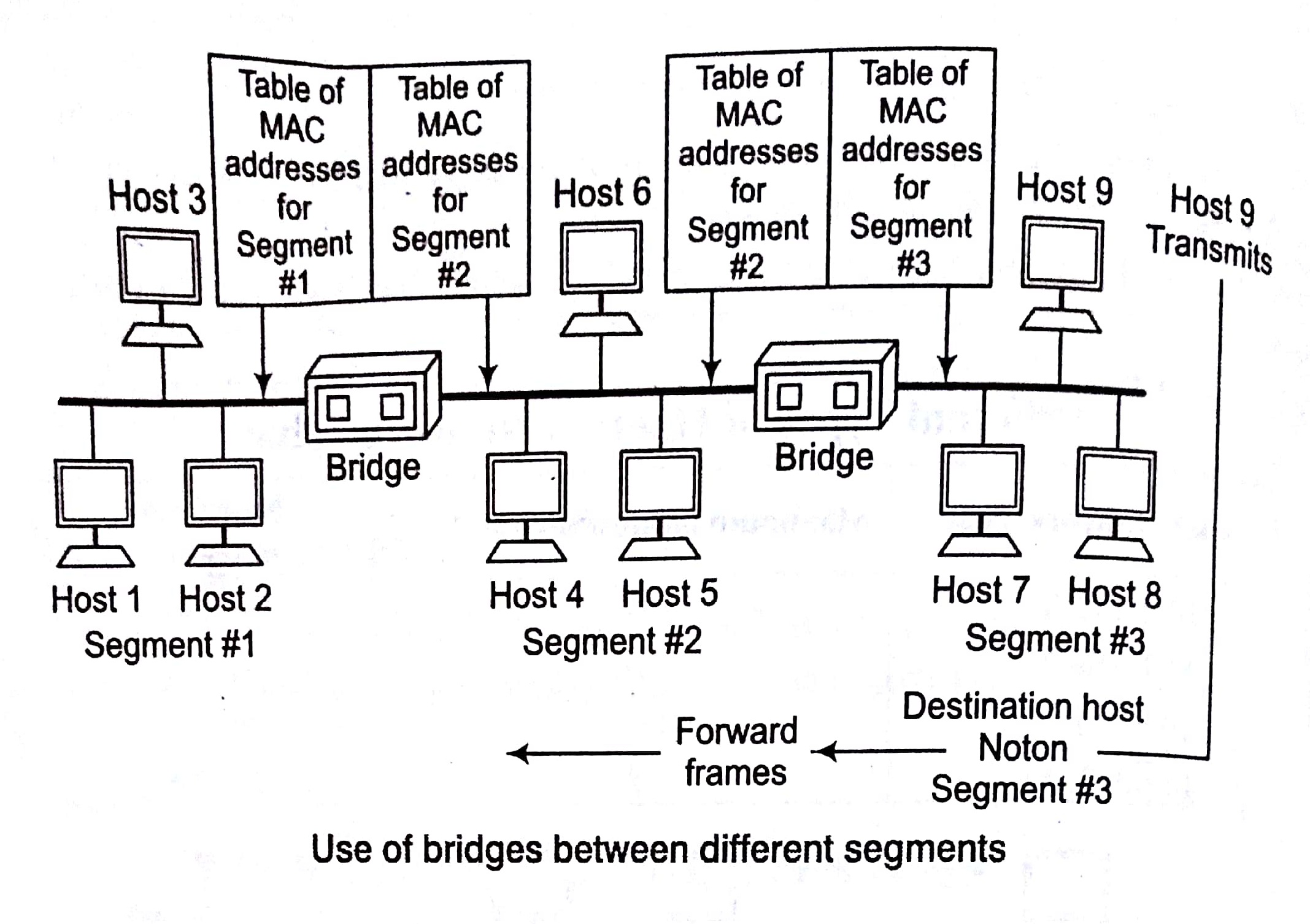
Key Points
- Bridges map the addresses of the nodes residing on each network segment and allow only necessary traffic to pass through the bridge
- When a packet is received be the bridge, the bridge determines the destination and source segments.
- If the segments are the same, the packet is filtered, if the segments are different, then the packet is forwarded to the correct segments.
Switch
Switches are an expansion of the concept of bridging. LAN switches can link 4,6,10 or more networks together.
Cut through switches examine the packet destination address, only before forwarding it.onto its destination segment, while a store and-forward switch accepts and analyzes the entire packet before forwarding it to destination, while a store and-forward switch accepts and analyzes the entire packet before forwarding it to its destination. It takes more time to examine the entire packet, but it allows to catch certain packet errors and keep them from propagating through the network.
Routers
Router forwards packets from oneLAN (orWAN) network to another. It is also used at the edges of the networks to connect to the Internet.
Gateway
Gateway acts like an entrance between two different networks. Gateway in Gateway in organizations, , is the computer that routes the traffic from a work station to the outside network that is serving web pages.
ISP (Internet Service Provider) is the gateway for Internet service at homes.
Some IEEEStandards for Networking
| Standard | Related to/Used for |
| IEEE 802.2 | Logical Link Control |
| IEEE 802.3 | Ethernet |
| IEEE 802.5 | Token Ring |
| IEEE 802.11 | Wireless LAN |
| IEEE 802.15 | Bluetooth |
| IEEE 802.16 | Wireless MAN |
Key Points………………………………………………………………………………………………
- Switches have 2 basic architectures: cut through and store-and-forward.
- Switching is a technology that alleviates congestion in Ethernet LANs by reducing traffic and increasing bandwidth.
- It operates in the third layer and forwards packets based on network addresses using routing tables and protocols.
- Gateway’s main concern is routing traffic from a work station to the outside
Ethernet
It is basically a LAN technology which strikes a good balance between Speed, cost and easy of installation. The Institute for Electrical and Standard Engineering (IEEE) defines the Ethernet Standard as IEEE standard 802.3. This standard defines rule for configuring an Ethernet network as well as specifying how elements in an Ethernet network interact With each other.
Ethernet uses Carrier Sense Multiple Access/Collision Detect (CSMA/CD) technology, broadcasting each from onto the physical medium (wire fiber and so on). All stations attached to the Ethernet listen to the line for traffic and the station with the matching destination MAC address accepts the frame.

Ethernet 221.22.0.3 diagram
Token Ring
- It is another form of network configuration, which differs from Ethernet in that all messages are transferred in a unidirectional manner along the ring at all times.
- Medium Access Control (MAC) is provided by a small E Free token frame, the token that circulates around the ring when all stations are idle. Only the station (node) possessing the token is allowed to transmit at any given time. Sender looks for free token and changes free token to busy token and appends data.
- This technology can connect upto 255 nodes in a physical star or ring connection that can sustain 4 or 16 Mbps.
FDDI (Fiber Distributed Data Interface)
This is a form of network configuration, which uses a ring topology of multimedia or single mode optical fiber transmission links operating at 100 Mbps to span upto 200 km and permits upto 500 stations. It employs dual counter rotating rings. Here, 16 and 48 bit addresses are allowed. In FDDI, token is absorbed by station and released as soon as it completes the frame transmission.
Sorting in Design and Analysis of Algorithm Study Notes with Example
Learn Sorting in Handbook Series: Click here
Follow Us on Social Platforms to get Updated : twiter, facebook, Google Plus
