Basics of Computer Hardware Course in Cyber Security with Examples
Basics of Computer Hardware Course in Cyber Security with Examples:-In this cyberpointsolution tutorial we are going to describe about the concept of Hardware Component which is used in ethical hacking cyber programming. And also we will describe that how can we use computer hardware in ethical hacking for our safety. And why we use ethical hacking to make more interactive and secure for our daily life. When ever we want to learn any thing the things become more earlier is somebody/tutorial/study material taught us through Examples. Here we have tried to describe each and every concept of computer hardware course with examples in the light of cyberpointsolution.com best Hindi Short tutorial using simple and best possible example. These examples are so simple that even a beginner who had never even heard about hacking and Cyber law can easily learn and understand How the Ethical Hacking works in our today’s Technical Field. This is the best tutorial/Study Material very beneficial for beginners as well as Professional.
What is Computer Hardware
Computer hardware includes the physical, tangible parts or components of a computer, such as the cabinet, central processing unit, monitor, keyboard, computer data storage, graphic card, sound card, speakers and motherboard.
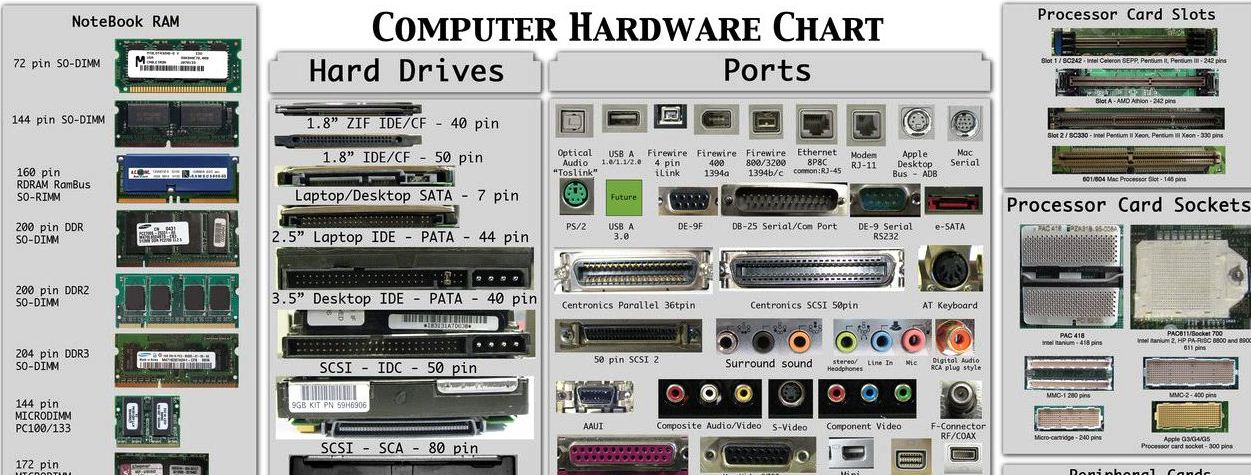
By contrast, software is instructions that can be stored and run by hardware.
Hardware is so-termed because it is “hard” or rigid with respect to changes or modifications; whereas software is “soft” because it is easy to update or change.
What is SMPS-
Switched Mode Power Supply. They convert AC power into DC power and decide which h/w component need how much current.
Power connector types of SMPS
- AT (6+6=12 pins)
- ATX (20 pins)
- BTX (24 – 28 pins)
If SMPS is not working take black and green wire and connect it It fan rotate it is Ok , If fan is not rotate the problem in SMPS.
MOLEX CONNECTOR
4 Pin peripheral power connector. Power to many devices in the computer.
(adsbygoogle = window.adsbygoogle || []).push({});
Example:- Storage device, optical drive, fan, other peripherals
ATX
Give power to motherboard.
RAM:- (Random Access Memory)- It is a volatile memory, it temporary store the data. In order for a program to run, it needs to be loaded into RAM first.

DYNAMIC RAM:-
- Contains capacitors
- Capacitors have to be refreshed with electricity constantly Capacitor (0 and 1)
DRAM stores each bit of data as program code in a storage cell consisting of a capacitor. A DRAM storage cell is dynamic is that it need to be refreshed or given a new electronic charge every few milliseconds to compensate for charge leaks the capacitor.
STATIC RAM
Static Ram is a type of RAM that holds data in a static forms, that is as long as the memory has power unlike dynamic RAM, it does not need to be refreshed.
DRAM V/S STATIC RAM
- Static Ram is used in catch memory
- Dynamic Ram is used in main memory.
- SRAM is fast
- DRAM is slow
Architecture of RAM
- SIMM (Single in Line Memory Module)
32 bit data path
- DIMM (dual in-line memory module)
Transfer 64 bits of data at a time.
- RDIMM (Registered DIMM)
DIMM with improve reliability.
- DDR (Dual Data Rate)
Sends double the amount of data in each cbck signal. It has 184 pins.
- DDR2
It is faster than DDR because it allows for higer bus speeds. Use less power compare to DDR. It has 240 pins.
- DDR3
Twice fast comparison DDR2. Use less power then DDR2.It has 240 pin.
- DDR4
Use less power then DDR3. It has 288 pin.Process higher speed than DDR3.Use less power.
ROM:-
- Bios and booting module is stored in ROM.(Read Only Memory) – It is a Non-volatile memory. Data in ROM is permanently return and is not erased when you power off your computer
What is SOCKET
Physical connection b/w motherboard and Processor. (where processor fit) responsible for transmitting energy to the Processor
Types
- LPA (LAND GRID ARRAY)
- PGA (PIN GRID ARRAY)
CORE
(adsbygoogle = window.adsbygoogle || []).push({});
Responsible for processing speed. More core processor has more function simultaneously performed without overloading you system.
MULTI THREADING
It is double the no. Of core of processing.
PCI Slot (Peripheral Component Interconnect) –
- PCI – big size
- PCI express x16, x1

In 2004 new version PCI express PCI express slot is very fast compare PCI slot.
MEMORY
Memory is device where the data temporary of permanently store. According to storage there are two types of memory
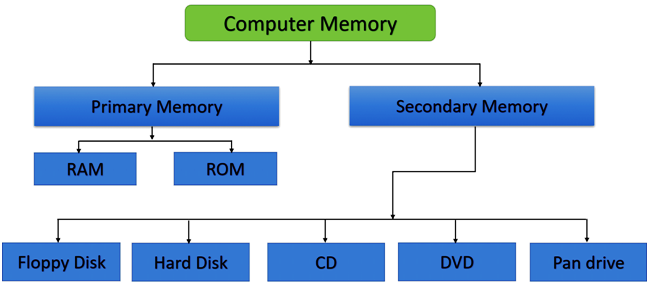
HARD DISK
Hard Disk is magnetic storage device it is also Secondary Memory data permanently store on the HDD.
- SATA (Serial ATA) –7PINS
- PATA , ATA (Parallel Advanced Technology Attachment)– 40 PINS
- SCSI (Small Computer System Interface)– (60-80 PINS)
- SSD (SOLID STATE DRIVES)

WHAT IS PARTITION
When logical divided of track is called partition. There are three types of partition.
- Primary
- Extended
- Logical
HEAT SINK
It is absorbed the unwanted heat of CPU and throw throw it out through fan.
SOUTH BRIDGE

North Bridge

CPU PORTS—
- PS2 PORT– USE FOR CONNECT KEYBOARD AND MOUSE
Purple– keyboard Green– Mouse
- USB Port– 2.0, 3.0, 3.1-latest
- Lan Port Or NIC Card– to connect to ethernet cable.
- Audio port– MIC — Pink
Headphone– Green
Audio out — Blue
- VGA Port– To connect display to cpu. 9pins
- HDMI port– high display multimedia interface
Used for to watch HD video in display.
- DVI Port– Support digital signal
If we use DVI port for display, we have to external audio port for audio as it only support video.
Expension slot—To add extra ports to cpu
Parrallel advanced Technology Attachment
40 pin
Data transmission is parallel
BIOS (Basic Input Output System) – The information all hardware ports (I/O) are store. In BIOS chip, BIOS first check all hardware path if all ports are working then start the PC and No any device found it give error.
1.bios
2.UEFI

CMOS Battery – CMOS(Complementary Metal-oxide Semiconductor)
Battery provide a power supply of BIOS chip to maintain date and time.
It have two size
CACHE MEMORY – Self memory of processor is called cache memory there are three types of cache memory
PARTITON OF HARD DISK
- MBR (Master Boot Record ) – The area of hard disk which is used to detect BIOS and start the booting process of HDD(Track 0, Sector 0, Cylinder 0)
- GPT (GUID Partition Table)(Globally Unique Identify) – It is same of MBR. All Morden PC Operating System Support GPT including MAC OS and Windows OS.
| MBR | GPT |
| • MBR was first introduce by IBM in 1983
• It use MBR the capacity of one partition in 2 TB • MBR support maximum 4 Primary Partition. |
• GPT was latest and introduce by MICROSOFT.
• GPT use unlimited spaces . GPT support 128 Primary Partition |
FILE SYSTEM
format is method to create allocation table of any storage media and the process complete with help file system.
There are following File System
- FAT (File Allocation Table)
- FAT-32
- NTFS (New Technology File System)
- CDFS (CD/DVD)

MINIMUM HARDWARE REQUIRE TO INSTALL Window
| Facility | Bit | Windows 10 | Windows 8/ 8.1 | Windows 7 |
| Processor | 32-bit | 1 GHz or Higher | 1 GHz or Higher | 1 GHz or Higher |
| 64-bit | 1 GHz or Higher | 1 GHz or Higher | 1 GHz or Higher | |
| RAM | 32-bit | 1 GB | 1 GB | 1 GB |
| 64-bit | 2 GB | 2 GB | 2 GB | |
| Free Hard Disk Space | 32-bit | 16 GB | 16 GB | 16 GB |
| 64-bit | 20 GB | 20 GB | 16 GB | |
| Graphics Card | DirectX 9 Graphics With WDDM 1.0 or Higher Driver | DirectX 9 Graphics With WDDM 1.0 or Higher Driver | DirectX 9 Graphics With WDDM 1.0 or Higher Drive |
Deployment type of OS
- COS (CLIENT OPERATING SYSTEM)
The Client Operating System is the system that works within computer desktops and various portable devices. This system is different from centralized servers because it only supports a single user. Smartphones and small computer devices are able to support client operating systems
- NOS-(NETWORK OPERATING SYSTEM)
A network operating system (NOS) is a computer operating system system that is designed primarily to support workstation, personal computer, and, in some instances, older terminal that are connected on a local area network (LAN).
- SOS –(SERVER OPERATING SYSTEM)
A server operating system (OS) is a type of operating system that is designed to be installed and used on a server computer. It is an advanced version of an operating system, having features and capabilities required within a client-server architecture or similar enterprise computing environment.
DNS (Domain Name Server)
- Type ipconfig /flushdns and press Enter.
- Type ipconfig /registerdns and press Enter.
- Type ipconfig /release and press Enter.
- Type ipconfig /renew and press Enter.
- Type ipconfig /displaydns and press Enter.
Dns cache
A DNS cache (sometimes called a DNS resolver cache) is a temporary database, maintained by a computer’s operating system, that contains records of all the recent visits and attempted visits to websites and other internet domains.
SAM(Security Account Manager)
The Security Account Manager (SAM), often Security Accounts Manager, is a database file in Windows XP, Windows Vista, Windows 7, 8.1 and 10 that stores users’ passwords. It can be used to authenticate local and remote users. Beginning with Windows 2000 SP4, Active Directory authenticates remote users
C:\Windows\System32\config
C:\windows\system32\config\SAM
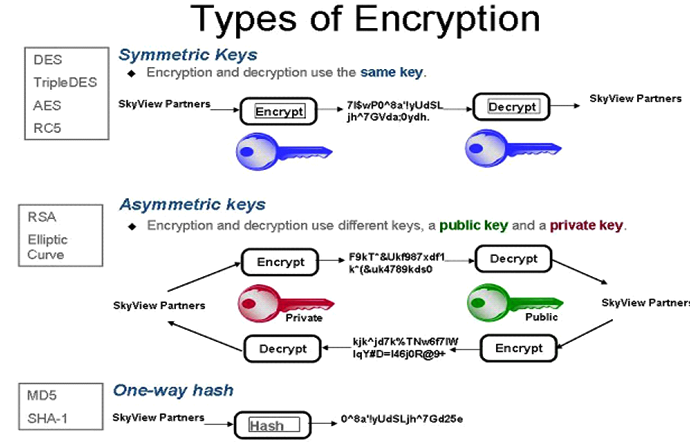
Encryption
The translation of data into a secret code. Encryption is the most effective way to achieve data security. To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it. Unencrypted data is called plain text; encrypted data is referred to as cipher text.
- AES. The Advanced Encryption Standard,
- Triple Data Encryption Standard
- Rivest Shamir Adleman
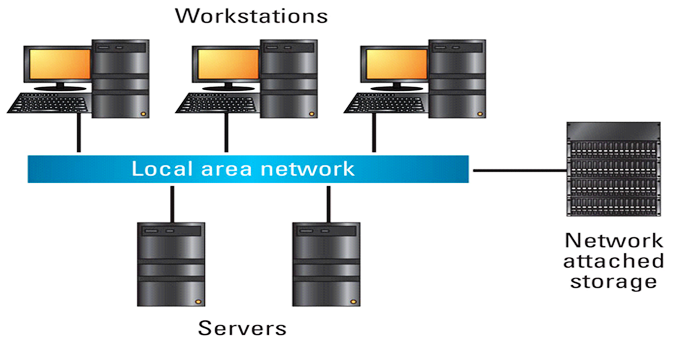
NAS
Network-attached storage (NAS) is a file-level computer data storage server connected to a computer network providing data access to a heterogeneous group of clients. NAS is specialized for serving files either by its hardware, software, or configuration.
For Other More Computer Hardware Component which is used in Cyber Security and Hacking Means Ethical Hacking. Click For on this link For the Next Page like Rubber Ducky, Raspberry pi etc links are given below
Follow Us On Cyber Point Solution Youtube Channel : Click Here
Follow Us on Social Platforms to get Updated : twiter, facebook, Google Plus
Learn More Ethical Hacking and Cyber Security click on this link. cyber security
