Software Risk Management Tutorial Tools and Techniques with Examples
Software Risk Management Tutorial Tools and Techniques with Examples:The Complete Guide of Computer Science and Information Technology to Crack any Examination:-In this cyberpoint9 tutorial we are going to describe about the concept of Any Competitive Examination in Computer Science and Information Technology and cyber programming. And also we will describe that how can we crack any Competitive Examination Like GATE-CS ,UGC-NET,BARC,VSSC, DRDO, ISRO, NASA, BHEL,SPACEX,GOOGLE,FACEBOOK, etc .This is the free Full Complete Guide for Computer Science and Information Technology Students and Achievers Scientist.In this tutorials: course for Beginners to Advance And why we use Handbook of CS AND IT to make more interactive and save our time for our Daily life. Best Online Tutorial for Computer Science and It students .When ever we want to learn any thing the things become more earlier is somebody/tutorial/study material taught us through Examples. Here we have tried to describe each and every concept of Programming and Cyber Security in the light of cyberpoint9.com best Hindi Short tutorial using simple and best possible example. These examples are so simple that even a beginner who had never even heard about hacking and Cyber law can easily learn and understand How the isro and barc drdo for computer science books works in our today’s Technical Field. This is the best tutorial/Study Material very beneficial for beginners as well as Professional.The Complete Guide of Computer Science and Information Technology.
Software Risk Management
Risk is a problem that could cause some loss or threaten the success of the project but which has not happened yet. Risk management means dealing with a concern before it becomes a crisis.
Typical Software Risks
These can be classified as
Requirement Issue
Many project face uncertainty around the products’s requirements. If we do not control requirements related risk factors, we might either build the wrong product or build the right product badly.
Management Issue
Project manager usually write the risk management plan and most people do not wish to air the weaknesses in public. If we do not confront such touch issues, we should not be surprised, if they bite us at some points.
Lack of Knowledge
The rapid rate of change in technologies and the increasing change of skilled staff, means that our project team may not have the skills we need to be successful.
Risk management activities
Risk management activities consists of two key areas that are risk assessment and risk control.
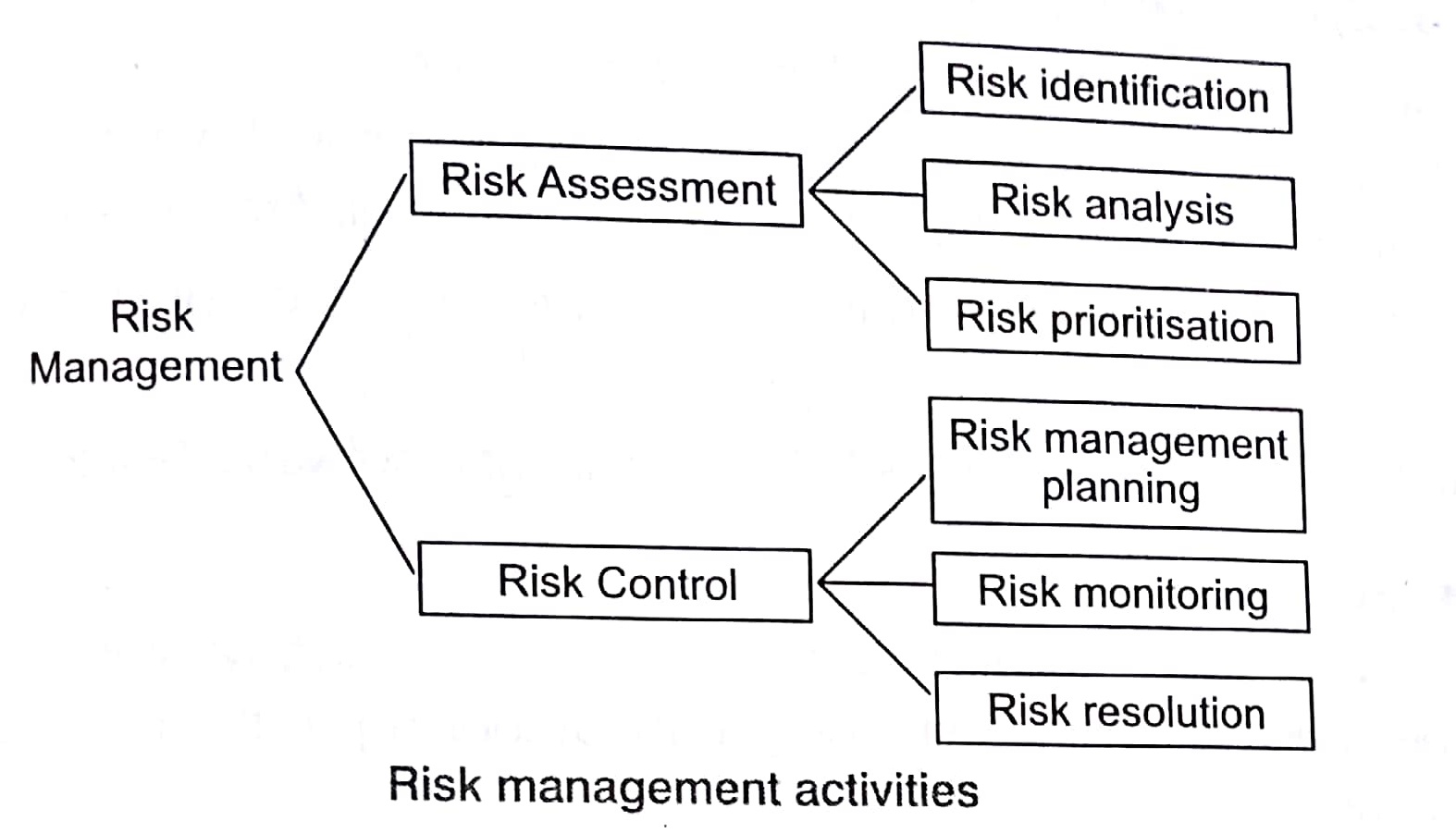
Risk Assessment
It is the process of examining a project and identifying areas of potential risk. Risk identification can be facilitated with the help of a check list of common risk areas of software projects. Risk analysis involves examining how project outcomes might change with modification of risk input variables. Risk prioritization helps the project focus on its most severe risks of assessing the risk exposure.
Risk Control
It is the process of managing risks to achieve the desired outcomes. Risk Management planning produces a plan for dealing with each significant risk. We should also monitor the project as development progress by periodically re-evaluating the risks and their probabilities. Risk resolution is the execution of the plans for dealing with each risk.
Risk Estimated Method
Priority of each risk can be computed as
P =r* s
where, r. The likelihood of a risk coming true.
s = The consequences of the problems associated with .that. risk.
Sorting in Design and Analysis of Algorithm Study Notes with Example
Learn Sorting in Handbook Series: Click here
Follow Us on Social Platforms to get Updated : twiter, facebook, Google Plus
