Security Services in Computer Network Security Tutorial with Examples
Security Services
These are two main categories of security services
RFC 2828: It defines as a processing or communication service provided by a system to give a specific kind of protection to system resources.
X.800: It defines as a service provided by a protocol layer communicating open systems, which ensures adequate security of systems or of data transfers.
X.800 Classification
800 defines it in five major categories
- Authentication Assurance that the communicating is the one clam–
- Access Control Prevention of the unauthorized use of resources.
- Data Confidentiality Protection of data from unauthorized
- Data integrity Assurance that data received is as sent by as authorized entity.
- Non-Repudiation Protection against denial by one of the Communication.
Security Mechanism
Feature designed to detect, prevent or recover from security attack.
The Two categories of security mechanism are as follows.
Specific Security Mechanism
Encipherment digital signature, access control, data integrity, authentication exchange, traffic padding, routing control, notarization.
Pervasive Security Mechanism
Treated functionality, security labels, event detection, security audit trails, security recovery.
Security Attacks
it is an action that compromises the security of information owned by an organisation.
These are two types of security attacks
Passive Attacks
Eavesdropping on or monitoring— of transmission to
- Obtain message contents 1 Monitor traffic flows
Active Attacks
In computer and computer network an attack is any attempt to destroy, expose, after, disable, steal or gain unauthorized access to or make unauthorized use of an asset. Modification of data stream to
- Masquerade of one entity as some other
- Replay previous messages
- Modify messages in transit
- Denial of service
Model for Network Security
Network security starts with authenticating, commonly with a username and password. since, this requires just one detail authenticating the user name i.e., the password this is some times teamed one factor authentication.
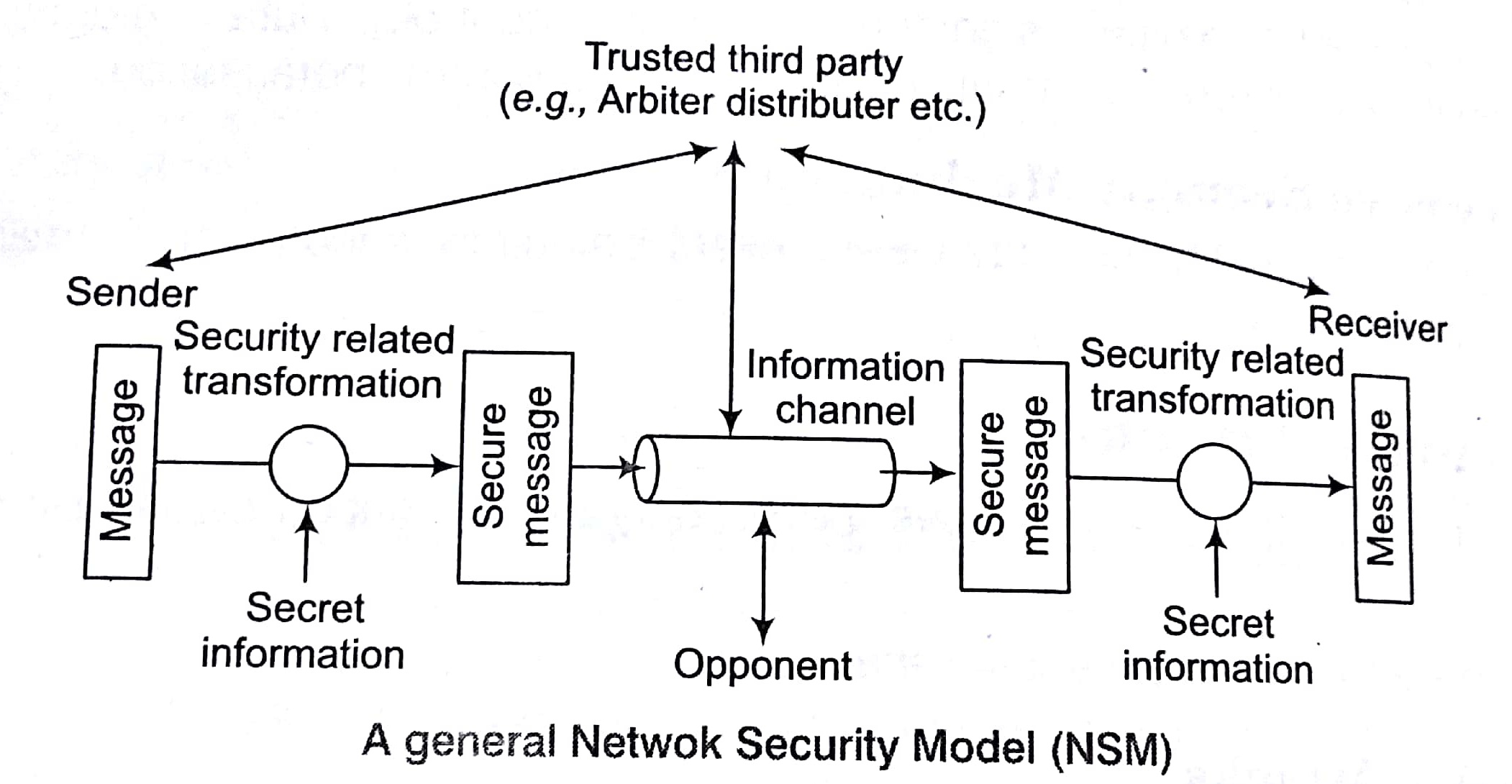
Using this model require us to
- Design a suitable algorithm for the security transformation.
- Generate the secret in formations (keys) used by the algorithm.
- Develop methods to distribute and share the secret information.
- Specify a protocol enabling the principles to use the transformation and secret information for security service.
Sorting in Design and Analysis of Algorithm Study Notes with Example
Learn Sorting in Handbook Series: Click here
Follow Us on Social Platforms to get Updated : twiter, facebook, Google Plus
