Purpose of Addressing Modes in Computer Architecture Tutorial with Examples
Addressing Modes
Addressing modes are the ways how architectures specify the address of an operand of an instruction. There are various addressing modes
Implied Mode
In this mode the operands are specified implicitly in the definition of an instruction.
Immediate Mode
In this mode the operand is specified in the instruction itself or we can say that, an immediate mode instruction has an operand rather than an address.
Register Mode
In this mode, the operands are in registers.
Direct Address Mode
It this mode, the address of the memory location that holds the operand is included in the instruction. The effective address is the address part of the instruction.
Indirect Address Mode
In this mode the address field of the instruction gives the address where the effective address is stored in memory.
Relative Address Mode
In this mode the content of program counter is added to the address part of the instruction to calculate the effective address.
Indexed Address Mode
In this mode, the effective address will be calculated as the addition of the content of index register and the address part of the instruction.
Data Transfer Instructions
Data Transfer Instructions cause transfer of data from one location to another without changing the information content.
The common transfers may be between memory and processor registers, between processor registers and input/output.
Typical Data Transfer Instructions
Name Mnemonic
LOAD LD
STORE ST
MOVE MOV
EXCHANGE XCH
INPUT IN
OUTPUT OUT
PUSH PUSH
POP POP
Data Manipulation Instructions
Data manipulation instructions perform operations on data and provide the computational capabilities for the computer.
There are three types of data manipulation instructions.
- Arithmetic instructions
- Logical and bit manipulation instructions
- Shift instructions

Typical Logical and Bit Manipulation Instructions
Name Mnemonic
CLEAR CLR
COMPLEMENT COM
AND AND
OR OR
EXCLUSIVE-OR XOR
CLEAR CARRY CLRC
SET CARRY SETC
COMPLEMENT CARRY COMC
ENABLE INTERRUPT EI
DISABLE INTERRUPT DI

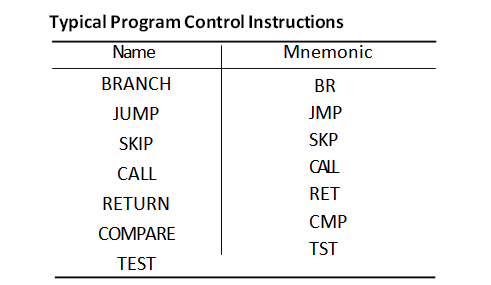
Program Control Instructions
- Program control instructions specify conditions for altering the content of the program counter, while data transfer and manipulation instructions specify conditions for data processing operations.
- The change in value of a program counter as a result of the execution of a program control instruction causes a break in the sequence of instruction execution.
Program Interrupt
- The program interrupts are used to handle a variety of problems that arise out of normal program sequence.
- Program interrupts are used to transfer the program control from a currently running program to another service program as a result of an external or internal generated request. Control returns to the original program after the service program is executed.
Types of Interrupts
There are three major types of interrupts
- External interrupt
- Internal interrupt
- Software interrupt
- External interrupts come from Input-Output (I/O). devices or from a timing
- Internal interrupts arise from illegal or erroneous use of an instruction or
- External and internal interrupts from signals that occur in the hardware of the CPU.
- A Software interrupt is initiated by executing an instruction.
Complex Instruction Set Computer (CISC)
- Computer architecture is described as the design of the instruction set for the processor.
- The computer with a large number of instructions is classified as a complex instruction set computer. The CISC processors typically have the 100 to 250 instructions.
- The instructions in a typical CISC processor provide direct manipulation of operands residing in memory.
- As more instructions and addressing modes are incorporated into a computer, the more hardware logic is needed to implement and support them and this may cause the computations to slow down.
Reduced Instruction Set Computer (RISC)
- RISC architecture is used to reduce the execution time by simplifying the instruction set of the computer.
- In the RISC processors, there are relatively few instructions and few addressing modes. In RISC processors, all operations are done within the registers of the CPU.
Design of Control Unit
- The function of the control unit in a digital computer is to initiate sequences of micro operations (the operations executed on data stored in registers are called micro operations).
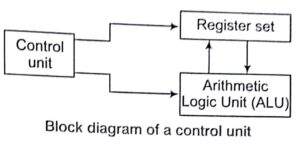
- The number of different types of micro operations that are available in a given system is finite.
- When the control signals are generated by hardware using conventional logic design techniques, the control unit is said to be hardwired.
- Microprogramming is a second alternative for designing the control unit of a digital computer.
Key Points
- The control unit initiates a series of sequential steps of micro operations. During any given time certain micro operations are to he initiated, while others remain idle.
- The control variables at any given time can be represented by a string of 1 s and 0 s called a control word.
Peripheral Devices
- The I/O system provides an efficient mode of communication between the central system and the outside environment.
- Programs and data must be entered into computer memory for processing End results obtained from computations must be displayed for the user. The most familiar means of entering ink .nation into a Computer is through a type writer-like keyboard. On the other hand the central processing unit is an extremely fast device capable of performing operations at very high speed.
- To use a computer efficiently, a large amount of programs and data must be prepared in advance and transmitted into a storage medium such as magnetic tapes or disks. The information in the disk is then transferred into a high-speed storage, such as disks.
- Input or output devices attached to the computer are called the peripheral The most common peripherals are keyboards, display units and Printers. Peripherals that provide auxiliary storage for the system are magnetic disks and tapes.
Input-Output Interface
- Input-Output interlace provides a method for transferring information between internal storage and external I/O devices.
- Peripherals are connected to the central processing unit with a special communication links (I/O bus).
- The I/O bus from processor is attached to all peripheral interfaces.
I/O Communication
- The is a need of I/O bus for communication between CPU and peripheral devices because of many reasons
(A).Data formats of internal memory of CPU and the peripheral devices (I/O devices) are different.
(B).Data transfer rates CPU and the I/O devices are different.
Asynchronous Data Transfer
- The two’ units such as CPU and I/O interface, are designed independently of each other. If the registers in the interface does not have a common clock (global clock) with the CPU registers, then the transfer between the two units is said to be asynchronous.
- The asynchronous data transfer requires the control signals that are being transmitted between the communicating
 units to indicate the time at which data is being transmitted.
units to indicate the time at which data is being transmitted.
Strobe Control
- Strobe is a pulse signal supplied by one unit to another unit to indicate the time at which data is being transmitted.

Block diagram Data I4-Valid data*. Strobe 14-Valid data- 1
Timing diagram Destination initiated for data transfer
- Strobe may be activated by either the source or the destination unit.
- The strobe pulse is controlled. by the clock pulses in the CPU. The data bus carries the binary information from source unit to the destination unit. In source initiated strobe for data transfer,. the strobe is a single line that informs the destination unit when a valid data word is available in the bus.
- But in destination initiated for data transfer it informs the source to provide the data. Then source unit places the data on the data bus.
Handshaking
- The disadvantage of the strobe method is that the source unit has no information whether the destination unit has actually received the data item, if the source unit initiates the transfer. But if the destination unit initiates the transfer it has no way of knowing whether the source unit has actually placed the data on the bus. The handshake method solves this problem.
- The basic approach of handshaking is as follows. In handshaking method, there are two control signals unlike strobe control method. One control signal is in the same direction as the data flow in the bus from the source to the destination. This signal is used to inform the destination unit whether there are valid data in the bus. The second control signal is in the other direction from the destination to the source. It is used to inform the source whether it can accept data.

Synchronous Data Transfer
In synchronous data transfer a global or shared clock is provided to both Sender and receiver. The sender and receiver works simultaneously.
Modes of Transfer
The information from external device is stored in memory information transferred from the central computer into an external device via memory unit. Hence, this data transfer between the central computer and devices is handled in various modes.
- Programmed I/O
- Interrupt- initiated I/O
- Direct Memory Access (DMA)
Programmed I/O
In this mode, each data item is transferred by an instruction in the program. The transfer is to and from a CPU register and peripherals. In the programmed I/O method, the CPU stays in a program loop until the I/O unit indicates that it is ready for data transfer. Once the data transfer is initiated, the CPU is required to monitor the interface to see, when the transfer can again be made. This is a time-consuming process since, it keeps the CPU busy needlessly.
Interrupt-initiated I/O
This mode removes the drawback of the programmed I/O mode. In this mode, interrupt facility is used to inform the interface to issue an interrupt request signal when the data are available from the device. In the mean time the CPU can proceed to execute another program.
In this cyberpointsolution.com we are trying to explain each and every concept of Purpose of Addressing Modes in Computer Architecture Tutorial with Examples
Direct Memory Access (DMA)
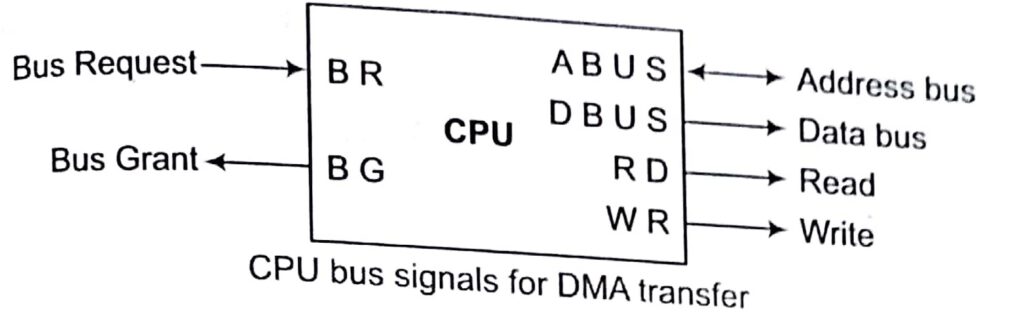
In programmed I/O mode, the transfer is between CPU and peripherals. But in direct memory access mode, the interface, transfers data into and out of the memory unit through the memory bus. The CPU initiates the transfer by supplying the interface with the starting address and the number of words needed to be transferred and then proceeds to execute other tasks. When the transfer is made, the DMA requests memory cycles through the memory bus. When the request is granted by the memory controller, the DMA transfers the data directly into memory.
The Bus Request (BR) input is used by the DMA controller to request the CPU to get the control of buses. When this input is active, the CPU terminates the execution of the current instruction and places the address bus and the data bus. The CPU activates the Bus Grant (BG) output to inform the external DMA that the buses are available. The DMA now takes the control of the buses to conduct the memory transfer. When DMA terminal the transfer, it disables the bus request line. The CPU disables the bus grant, takes the control of the buses.
Sorting in Design and Analysis of Algorithm Study Notes with Example
Follow Us On Cyber Point Solution Youtube Channel : Click Here
Follow Us on Social Platforms to get Updated : twiter, facebook, Google Plus
Learn More Ethical Hacking and Cyber Security click on this link. cyber security

Dejting kroatiska miljo-dejtingsajt ar Speed Dating en akta grej p4g dating Naoto Online Dating app for indiska https://3dlabs.co/dejtingsajter-toulouse.html Dating en franskild foralder