Medium Access Control Sublayer Tutorial in Computer Network with Examples
Medium Access Control Sublayer
The protocols used to determine, who goes next on a multi-access channel belong to a sublayer of the data link layer. This sublayer is called medium access control sublayer.
Channel Allocation
Static Channel Allocation FDM (Frequency Division Multiplexing) and TDM (Time Division Multiplexing) is used for this purpose. Let us focus on FDM, the mean time delay T for a channel having capacity C bit/sec, with an arrival rate of X frame/sec and each frame having a length drawn from an exponential probability density function with mean p, bits/frame. Then,
T=
C — X
If the channel is used by N independent sub-channels.
Then, 1 =________ = NT
TFDm =_____________ (C .
- N) (X/N) —
Dynamic Channel Allocation
In these methods, the channel is allocated to a particular system dynamically i.e., no predetermined order of senders for accessing the channel in order to send data.
Multiple Access Protocols
These protocols can be divided into two categories ALOHA
- Pure ALOHA . Slotted ALOHA
CSMA
- 1-persistent GSMA
- p_persistent CSMA
- Non-persistent CSMA
ALOHA Protocols
ALOHA net, known as the ALOHA system, or simply ALOHA, was pioneering computer networking. System developed at the university of Huwai. It was designed for a radio wireless LAN, but it can be used on any shared medium.
The ALOHA protocols can be of following types
Pure ALOHA: In this approach, a node, which wants to transmit will go ahead and send the packet on its broadcast channel with no consideration whatsoever as to anybody else is _ transmitting or not. One serious drawback here is that, we are not sure about whether the data has been received properly at the receiver end. To resolve this, the pure ALOHA‘ when one node finishes speaking, it expects an acknowledgement in a finite amount of time otherwise, it simply re-transmits the data.
Key Points
- Pure ALOHA: This scheme works well in small networks where the load is not
- In large load intensive networks where many nodes may want to transmit at the same time, the Pure ALOHA scheme fails miserably.
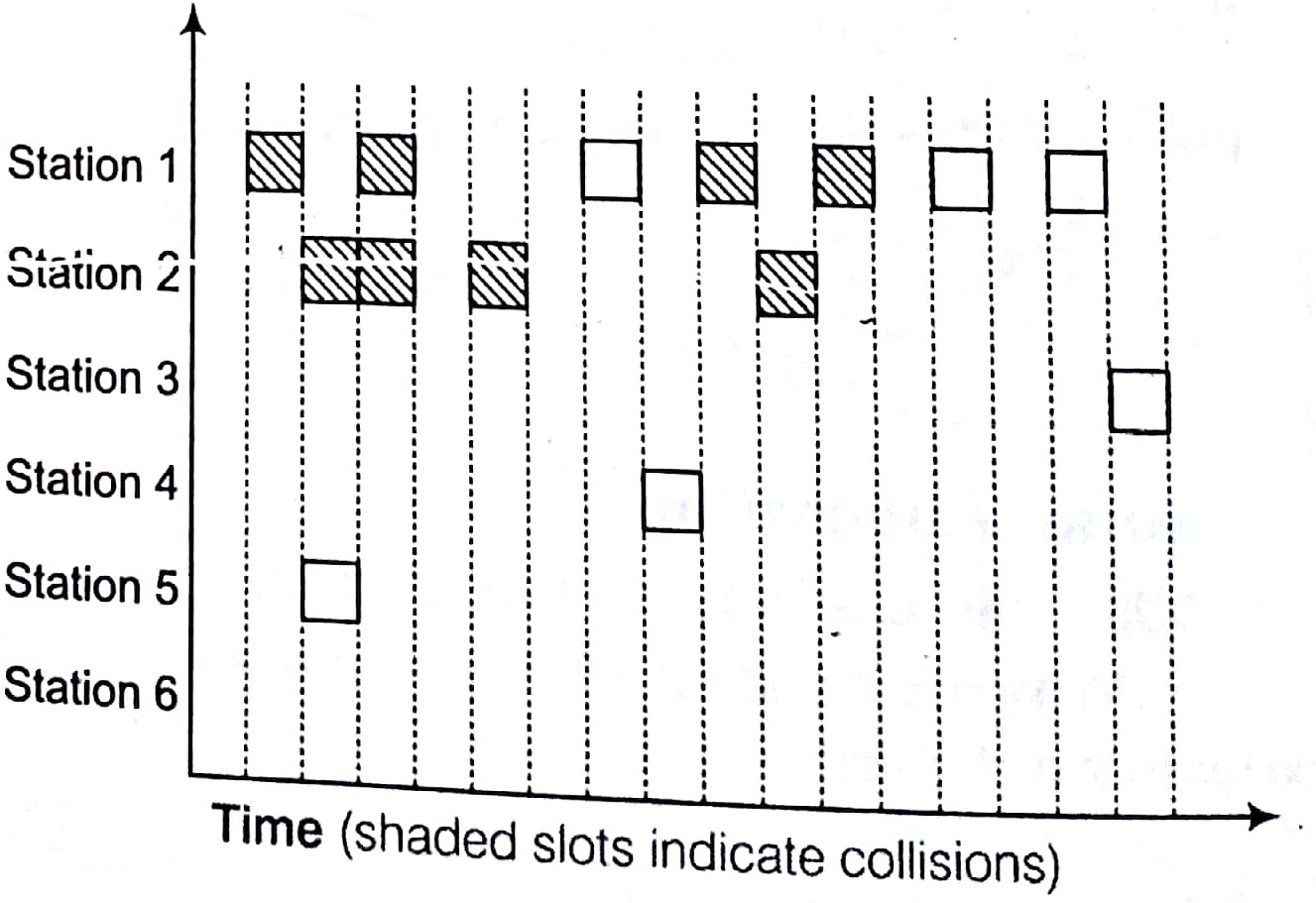
Slotted ALOHA :This is quite similar to pure ALOHA, differing only in. the way transmissions take place Instead of transmitting right at demand time, the sender waits for some time. This delay is specified as follows timeline is divided into equal slots and then it is required that transmission should take place only at slot boundaries.
To be more precise, the slotted ALOHA makes the following assumption
- All frames consists of exact L bits.
- Time is divided into discrete frame time salts i.e. ,a slot equals the time to transmit one frame.
- Nodes start to transmit frames only at the beginning of slots.
- The nodes are synchronized, so that each nodes knows when the slot
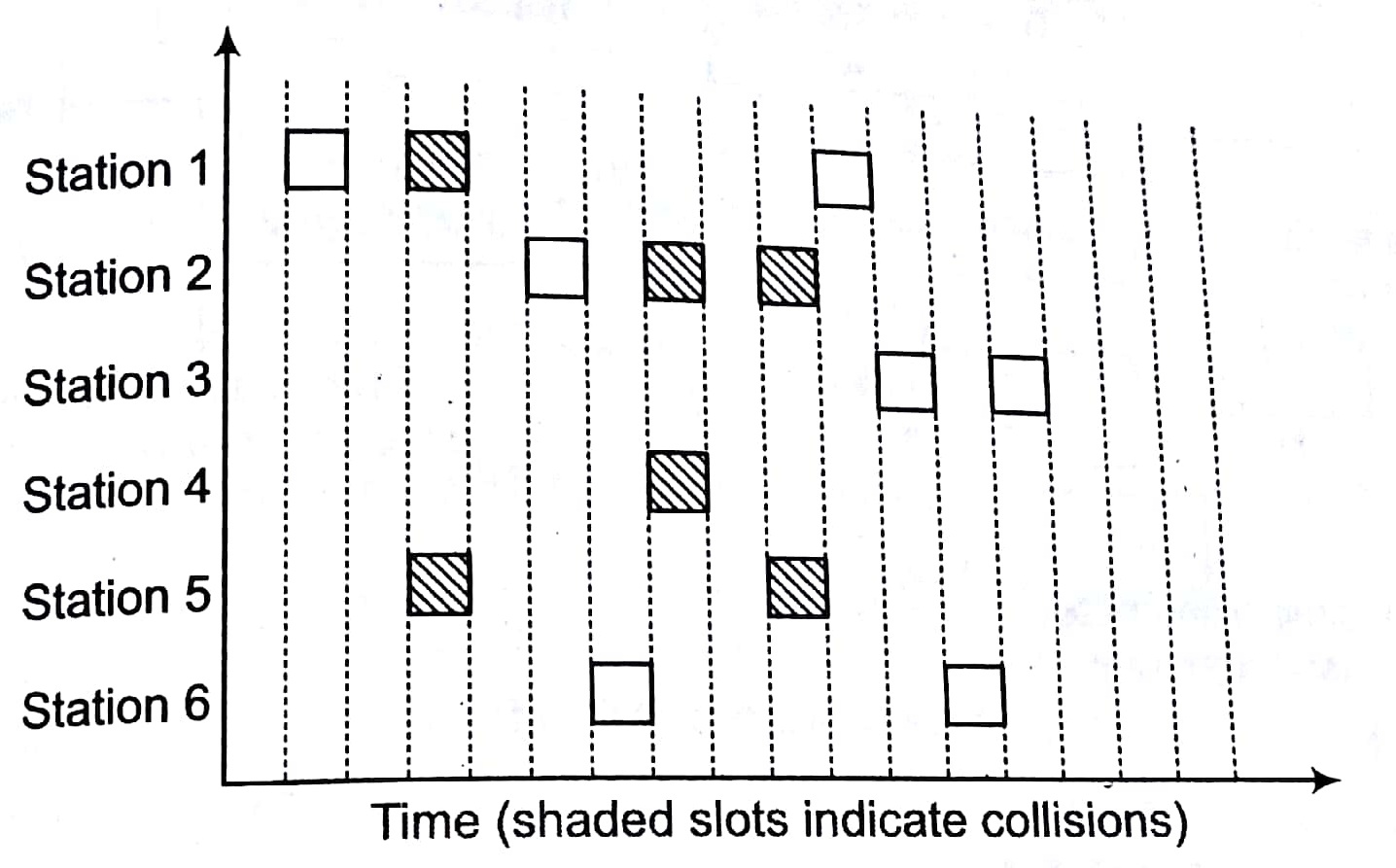
- If two or more frames collide in a slot, then all the node detect collision event before the slot ends.
Key Points……………………………………………………………………………………………….
- Whenever multiple users have unregulated access to a single line, there is a danger of signals overlapping and destroying each other. Such overlaps, which turn the signals into unusable noise are called collisions.
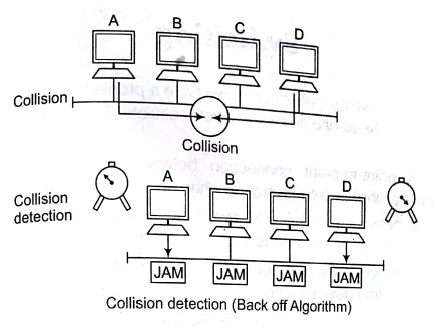
- A LAN therefore needs a mechanism to coordinate traffic, minimize the number of collisions that occur and maximize the number of frames that are delivered successfully. The access mechanism used in an Ethernet is called CSMA/CD, standardized in IEEE 802.3.
- Switches are hardware and/or software devices capable of creating temporary connections between 2 or more devices linked to the switch but not to each other.
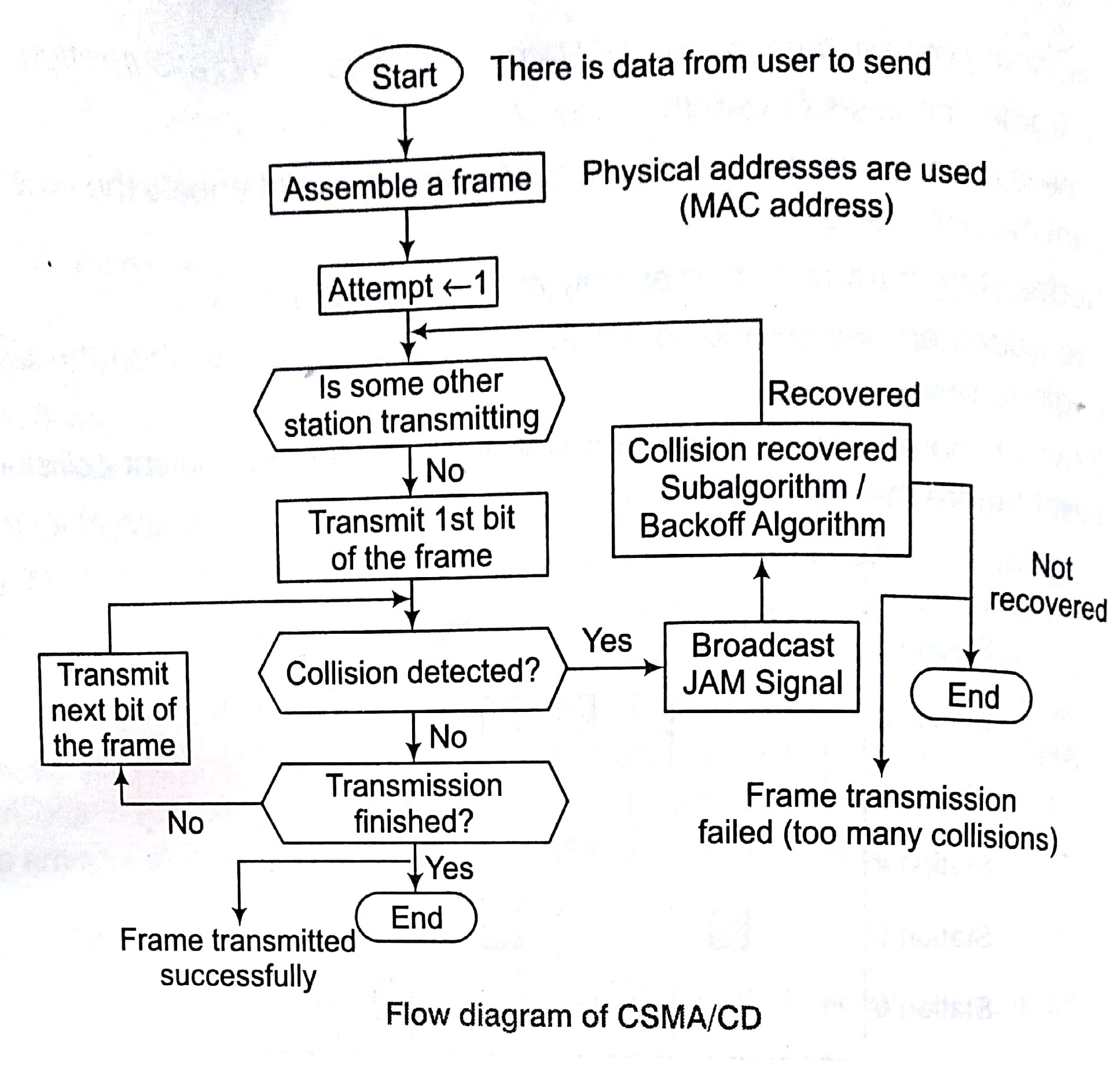
Carrier Sense Multiple Access/Collision Detection (CSMA/CD)
To minimize the chance of collision and, therefore increase the performances, the ,CSMA/CD was developed. The idea with carrier sense multiple access is to listen down the channels before a transmission takes place.
The nodes are synchronized, so that each nodes knows when the slot
Persistent CSMA
In this scheme, transmission proceeds immediately, if the carrier is idle. However, if the carrier is busy, then sender continues to sense the carrier until it becomes idle. The main problem here is that, if more than one transmitters are ready to send, a collision is guaranteed. In case of collision, stations wait for a random period of time before re-transmission.
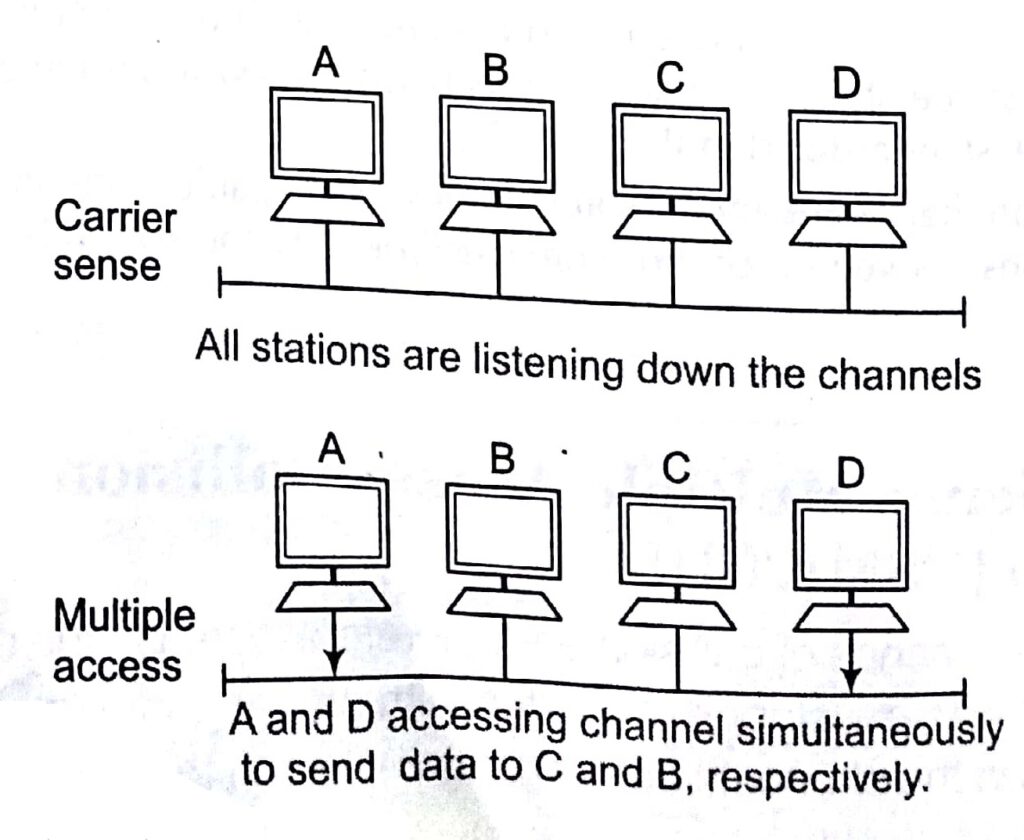
There are three types of CSMA approaches as given following
Non-persistent CSMA
In this scheme, the broadcast channel is not monitored continuously. The sender listens it at a random time intervals and transmits whenever the carrier is idle. This decreases the probability of collisions. But it is not efficient in a low load situation, where the number of collisions are anyway small. The problems it entails are
- If back-off time is too long, the idle time of carrier is wasted in some sense.
- It may results in long access delays.
P–Persistent CSMA
Even if a sender finds the carrier to be idle, it uses a probabilistic distribution to determine whether to transmit or not. Put simply “Toss a coin to decide”. If carrier is idle, then transmission take place with a probability P otherwise the sender waits with a probability (q = 1- p).
This scheme is good trade-off between the non- persistent and 1-persistent schemes . So, for low load situations, P is high (e.g., 1- persistent) and for high load situation , p may be lower.
Sorting in Design and Analysis of Algorithm Study Notes with Example
Learn Sorting in Handbook Series: Click here
Follow Us on Social Platforms to get Updated : twiter, facebook, Google Plus
