Counters in Computer Architecture Tutorial Study Notes with Examples
Counters
- Sequential circuit that goes through a prescribed sequence of states upon the application of input pulses is called a counter.
- In a counter, the sequence of states may follow a binary count or any other sequence of states.
- Counters are used for counting the number of occurrences of an event and are useful for generating timing sequences to control operations in a digital system.
- A counter that follows the binary sequence is called a binary counter.
- An n-bit binary counter consists of n flip-flop and can count in binary from 0 to 2″-1
- Up counters increases in value and down counters decreases in value.
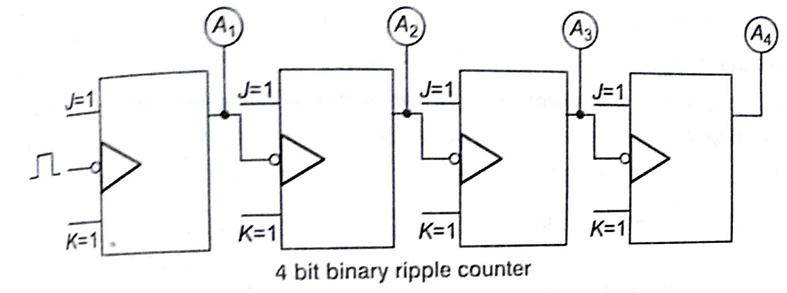
Asynchronous Counter (Ripple Counter)
In ripper counter tree flip-flop output transition serve as a source for triggering e.g., in a binary ripple counter consists of a series connection of complementing flip-flops (T or JK), with the output of each flip flop to the CP input of next higher order flip-flop.
Synchronous Counter
Synchronous counter is distinguished from ripple counter such that in synchronous counter clock pulses are applied to the CP inputs of all p-flop simultaneously, rather than one at a time in succession as in ripple counter.
The decision whether flip-flop is to be complemented or not is determined from the value of J and K inputs at the time of the pulse.
Registers
- A register consists of a group of flip-flops with a common clock input.
- Register are commonly used to store and shift binary data.
Key Points
An n bits register has a group of 0 flip-flop which can store a binary information of n bits.
Shift Register
It is a register in which binary data can be stored and then shifted left or right when a clock pulse is applied , Bits shifted out one end of the register may be either lost or shifted back in on the other end.
Sorting in Design and Analysis of Algorithm Study Notes with Example
Follow Us On Cyber Point Solution Youtube Channel : Click Here
Follow Us on Social Platforms to get Updated : twiter, facebook, Google Plus
Learn More Ethical Hacking and Cyber Security click on this link. cyber security
