What is Threat Modelling?
Threat modelling is a crucial cybersecurity process used to identify, analyze, and mitigate potential security threats to an application, system, or organization. This practice helps individuals and security teams understand how potential attackers might operate, allowing them to develop effective countermeasures to prevent these threats from being exploited.
Why is Threat Modelling Important?
- There are several reasons why developing a threat model is essential for organizations:
- Proactive Security: Identifying potential threats early in the software development life cycle enables security teams to implement protective measures before systems are deployed into production, significantly reducing the attack surface.
- Cost-Effectiveness: Addressing security vulnerabilities before they lead to breaches is generally more cost-effective than dealing with the aftermath of a system compromise.
- Compliance: Many regulatory frameworks, such as GDPR, HIPAA, and PCI-DSS, require organizations to demonstrate their ability to identify and mitigate security risks.
- Risk Mitigation: Threat modeling helps organizations understand the potential impact of security risks, assess their likelihood, and prioritize security efforts efficiently.
.
The Threat Modelling Process
The threat modeling process consists of four key steps: Identifying Assets, Creating an Architecture Overview, Identifying Threats, and Mitigating Threats.
- Identify Assets
Assets are valuable items or data that need protection, such as customer information, servers, applications, and cloud services. Identifying these assets helps determine what needs to be protected and from whom. - Create an Architecture Overview
An architecture overview is a high-level diagram representing the system or application, including components like servers, databases, APIs, user interfaces, and third-party services. This overview helps understand how data flows through the system, what sensitive data is stored, and how components interact. - Identify Threats
Threat identification involves analyzing the architecture to pinpoint potential security vulnerabilities and attack vectors. This step helps anticipate how an attacker might exploit weaknesses in the system. - Mitigate Threats
Mitigation strategies are developed to address identified risks. This step can involve two approaches: focusing on specific assets (risk management) or targeting particular attack patterns across the architecture. The goal is to reduce the likelihood and impact of potential attacks.
Several object-oriented threat modelling Frameworks, namely:
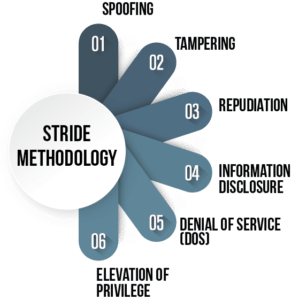
- STRIDE
STRIDE is frequently suited for use in object-oriented threat modeling, and it was introduced by Microsoft and includes six classes of threats: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. It assists you in taking any component of a system and determining if and how that component could present any one of these threats, then developing corresponding mitigations as necessary.
Advanced Application: For advanced application, STRIDE can be extended, namely its use with Data Flow Diagrams (DFDs), and incorporate automated tools that allow for continuous actual monitoring.
- DREAD
DREAD is a second framework that can be used to prioritize threats by evaluating five factors: Damage, Reproducibility, Exploitability, Affected Users, and Discoverability. It is distinctly different than STRIDE, in that STRIDE focuses on the types of threats, whereas DREAD is quantitative.
Advanced Application: For advanced threat modeling, DREAD can be used to assess risks dynamically as vulnerabilities emerge for an evolving system, to use risk cyclically, or continuously.
- ATT&CK Framework
The MITRE ATT&CK (Adversarial Tactics, Techniques, and Knowledge) framework is an application of very detailed and structured matrix excitings of attacks and techniques that attacks utilize at different phases of attacking. It provides very good detail, and a structured way to analyze adversary behavior over facets of TTPs.
Advanced Application: ATT&CK can be incorporated into sophisticated threat modeling to break down potential attack vectors and highlight gaps in existing defenses. The security teams may leverage ATT&CK by employing red team exercises or penetration tests by simulation against any potential attack with the associated attack matrices.
- PASTA (Process for Attack Simulation and Threat Analysis)
PASTA is a risk-centric threat modeling process that maps business objectives to technical requirements and starts from an attacker’s viewpoint. PASTA introduces a seven-stage process including defining objectives, scoping the threat landscape, performing a threat analysis, modeling the attack surface, modeling the relevant existing defenses, and finally conducting a conventional post-mortem review process that suggests remediation proposals.
For more Cybersecurity related content Follow: Cyber Point Solution, Youtube

1 Comment