LLMNR Poisoning: A Hidden Vulnerability in Windows Networks
In today’s enterprise environments, Windows-based networks rely heavily on Active Directory (AD) for managing resources and administrative tasks. However, with this convenience comes inherent risks, including one that is often overlooked—Link-Local Multicast Name Resolution (LLMNR) poisoning. This vulnerability can be exploited by attackers lurking within local networks, making it a serious concern for organizations that prioritize security.
In this article, we’ll dive deep into what LLMNR is, how it works, and how LLMNR poisoning attacks exploit its functionality. We will also cover effective LLMNR attack defenses, helping you secure your organization against this silent but dangerous threat.

What Is LLMNR?
Link-Local Multicast Name Resolution (LLMNR) is a protocol used by Windows systems to resolve hostnames when DNS requests fail. When a machine tries to communicate with a hostname and the DNS cannot provide an IP address, LLMNR kicks in, broadcasting the request to all systems within the local network. The NetBIOS Name Service (NBT-NS), a predecessor to LLMNR, serves the same purpose.
While these protocols help with local name resolution, they come with a significant security risk. If an attacker has infiltrated the network, they can intercept LLMNR queries and respond with false information, leading to LLMNR poisoning.
How LLMNR Poisoning Works
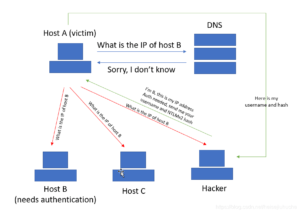
LLMNR poisoning exploits the design of the LLMNR protocol by intercepting name resolution broadcasts within a network. Here’s a step-by-step breakdown of how an LLMNR poisoning attack unfolds:
- DNS Failure: A user mistypes a network path (e.g., typing
\\shrefilesinstead of\\sharefiles), and the DNS server responds with “Not Found.” - LLMNR Broadcast: After DNS fails, the victim’s machine sends out an LLMNR query, asking if any device on the local network knows the IP address for
\\shrefiles. - Attacker Intercepts: A compromised machine running tools like Responder (preinstalled in Kali Linux) intercepts the LLMNR query and pretends to be the requested hostname.
- Victim Sends NTLM Hash: The victim machine attempts to authenticate with the attacker’s machine, sending its NTLMv2 hash.
- Hash Cracking: The attacker captures the hash and cracks it using tools like Hashcat with a commonly available wordlist, such as
rockyou.txt. If the password is weak, it can be cracked in seconds.
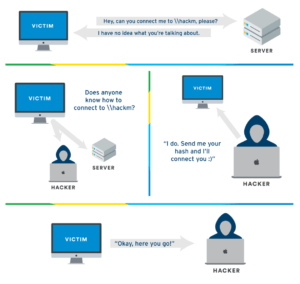
Once the attacker has cracked the NTLMv2 hash, they can escalate privileges, move laterally within the network, or steal sensitive data. In Active Directory environments, this can lead to full domain compromise.
How to Defend Against LLMNR Poisoning Attacks
The best way to protect your network from LLMNR poisoning is to disable LLMNR and NBT-NS entirely. These protocols are rarely needed in modern environments, and disabling them will eliminate this attack vector. Below are steps to secure your network:
1. Disable LLMNR
- Open Group Policy Editor.
- Navigate to Local Computer Policy > Computer Configuration > Administrative Templates > Network > DNS Client.
- Enable the setting for Turn off Multicast Name Resolution.
2. Disable NetBIOS
- Go to Control Panel > Network and Internet > Network and Sharing Center > Change Adapter Settings.
- Right-click on your active network adapter and select Properties.
- Double-click on Internet Protocol Version 4 (TCP/IPv4) and click Advanced.
- Under the WINS tab, select Disable NetBIOS over TCP/IP.
3. Enforce Strong Password Policies
Weak passwords significantly increase the success rate of LLMNR poisoning attacks. Implement strong password policies to ensure users are not using common or easily crackable passwords:
- Require passwords of at least 14 characters.
- Use a combination of upper/lower case letters, numbers, and symbols.
- Regularly rotate passwords and avoid reusing old passwords.
4. Implement Multi-Factor Authentication (MFA)
Even if an attacker successfully captures and cracks a user’s password, multi-factor authentication (MFA) provides an additional layer of security. With MFA, the attacker will still need access to a secondary form of verification, such as a hardware token or mobile app.
5. Enable SMB Signing
By enabling SMB Signing, you can ensure the integrity of SMB communications, reducing the risk of man-in-the-middle attacks like LLMNR poisoning. This can be configured through Group Policy.
Why Disabling LLMNR and NBT-NS Is Crucial
LLMNR and NBT-NS are legacy protocols that can be easily exploited by attackers within the local network. By disabling them, you can significantly reduce the attack surface and prevent a high-risk vulnerability from being exploited in your Active Directory environment.
Conclusion: Protecting Your Network from LLMNR Poisoning
LLMNR poisoning is an underappreciated threat that can compromise even well-secured networks. Attackers can exploit weak password policies and the LLMNR protocol to capture user credentials, potentially gaining access to privileged accounts. By disabling LLMNR and NBT-NS, enforcing strong password policies, and implementing multi-factor authentication, you can safeguard your organization from this type of attack.
This LLMNR poisoning guide provides a roadmap to improving your internal network security, ensuring that attackers cannot exploit name resolution vulnerabilities to compromise sensitive information.
Remember, proactive defense measures are key to securing your network in a world of ever-evolving cyber threats.
For more Cybersecurity related content Follow: Cyber Point Solution, Youtube
For any recommendations, please feel free to reach out to Riya jain

