A Guide to Implement CIS Controls with PowerShell
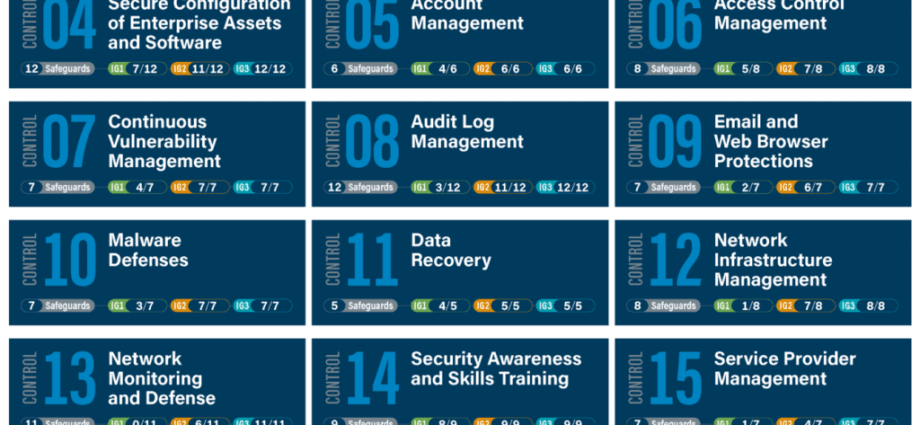
What is CIS? A Guide to Implement CIS Controls with PowerShell –Riya Jain In today’s interconnected world, cyber threats have become increasingly sophisticated, making it vital for organizations to adopt effective cybersecurity frameworks. The Center for Internet Security (CIS) provides a set of best practices known as the CIS Controls,Continue Reading