Step-by-Step Guide to Auditing Compliance via ManageEngine Endpoint Central
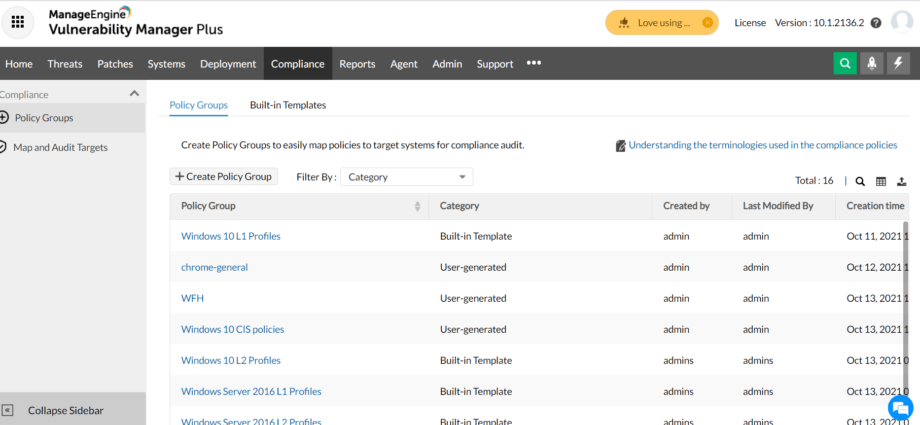
Step-by-Step Guide to Auditing Compliance via ManageEngine Endpoint Central –Riya Jain Maintaining security and compliance is essential for any organization, and ManageEngine Endpoint Central provides a powerful solution for automating and streamlining this process. Here’s a detailed guide on how to audit your environment using Endpoint Central. Step 1:Continue Reading